Recent ransomware attacks have put the spotlight on potential security vulnerabilities of some industrial Remote Access solutions. Around the world, users are scrambling to understand and mitigate these vulnerabilities.
Protecting automation endpoints from attacks that take advantage of remote connectivity is a vital concern for businesses that requires input and close collaboration from their Information Technology (IT), Operational Technology (OT), and security professionals.
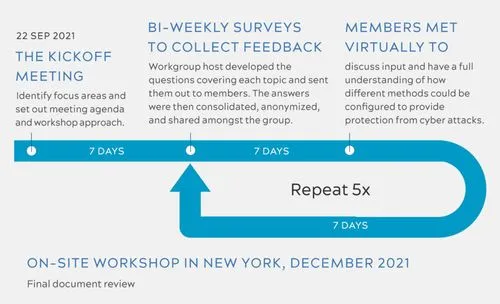
With this in mind, the Organization for Machine Automation and Control (OMAC) convened its second “Remote Access Workgroup,” to present practical, field-tested methods for reducing cybersecurity-related risk.
The workgroup, led by ei3, also reviews issues created by actors or processes that cause intentional or unintentional security incidents. This document is a follow-up to the initial OMAC document titled “Practical Guide for Remote Access to Plant Equipment” published in January 2021. It is recommended that the reader of this addendum first review that document to better understand all the aspects of remote access before taking a detailed look at security.